Honeypot Scams Explained: The Crypto Trap You Need to Avoid
Table of Contents
There have been many other incidents of people losing their valuable cryptocurrency assets to honeypot scammers. In this article, we will examine the techniques used in honeypot scams and ways to avoid them. But, before that, let’s discuss what honeypot scams are.
What is a Honeypot Scam?
A honeypot scam is a type of smart contract scam in which users can buy crypto tokens but cannot sell them, and in some cases, they may also get stolen. These scams are promoted by paid actors on various social media platforms, such as Telegram and TikTok, to deceive users into believing that everything is real and functional.
Various technical instruments are created, including liquidity, price movement, and transaction history, to lure users and make them buy tokens, and then silently block them from selling. Users’ funds are locked in a contract and can be withdrawn or transferred only by the scammer. Honeypot Scams are done mainly by engineering smart contracts on Ethereum and BNB Smart Chain. Scammers add malicious logic to the token’s code by using the programming language of Ethereum.
Techniques Used By Scammers
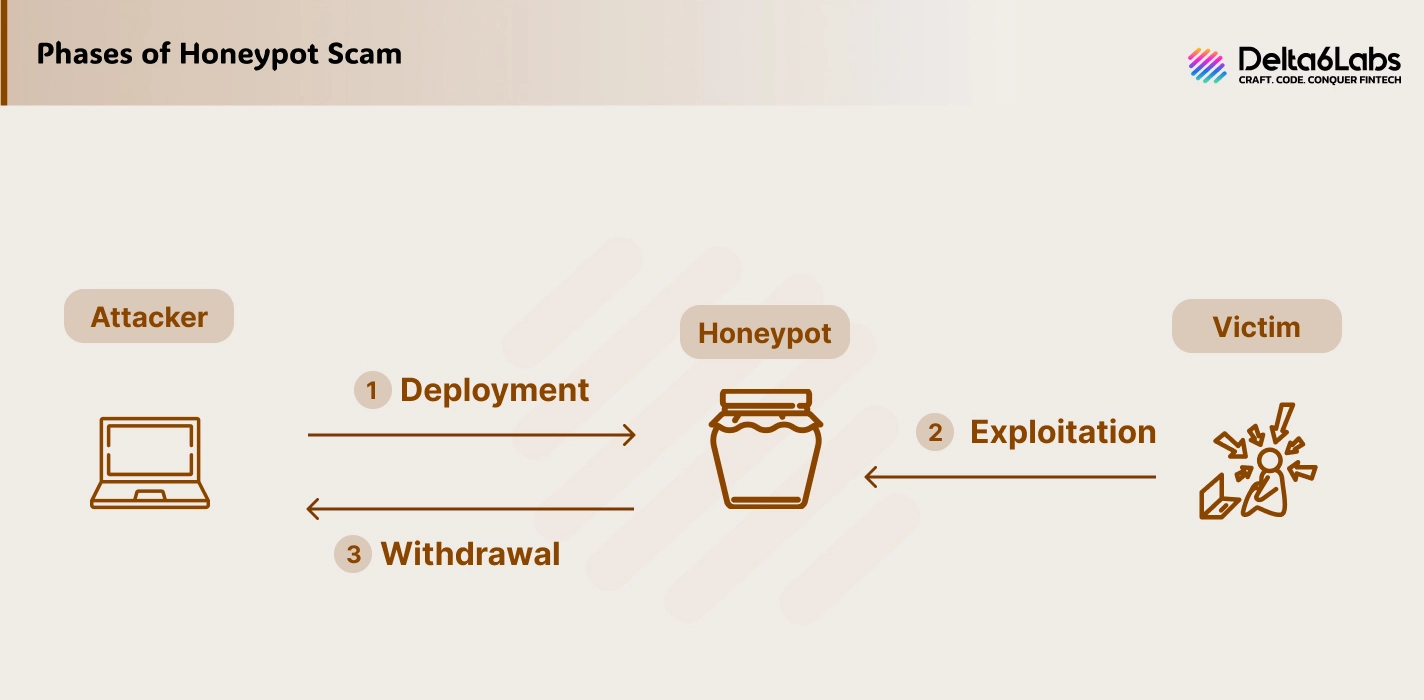
Here is the step-by-step process used by scammers to attract people into buying crypto tokens, only to get them blocked:
Token Creation and Promotion
Initially, a new token is created and promoted extensively through various platforms, including Telegram, Facebook, and WhatsApp. Fake ad campaigns are also utilized.
Fake Simulation
To make the token look real and popular, fake liquidity is injected along with fake trades and transaction histories. Social engineering tactics, such as the fear of missing out (FOMO), are also used to attract people to buy the asset before it becomes too expensive.
Withdraw
Once a trader purchases the token, the smart contract trap is triggered, and the tokens are blocked from selling and redeeming. The scammer has already set all the permissions to withdraw to himself. The crypto assets have vanished from the account by the scammer, creating an illusion that the token is still there, yet it can’t be redeemed or sold.
How To Check For a Honeypot Scam
Here are a few things to check for red flags that can save you from falling into the trap:
- Buy a small amount and try to sell it immediately. If the sell order fails, it’s possibly due to a honeypot scam.
- Tools like Token Sniffer and DexTools can identify red flags, including those in a honeypot scam.
- Thoroughly conduct a check on the token’s allocation mechanism, also known as tokenomics.
- If anyone shares a seed phrase or a secret recovery phrase, it is likely a scam. People using self-custodial wallets do not generally share their seed phrases.
Best Practices to Avoid Honeypot Scams
- The foremost thing that needs to be done to avoid honeypot scams is to conduct thorough market research and not rely entirely on information shared on social media and ads. It is also crucial to check whether the smart contract is verified on a reputable blockchain. You can also get the code reviewed by someone with coding knowledge.
- Keep a track of the trading activity to identify suspicious trading patterns, such as the absence of sell orders or unexplained liquidity removals.
- Conduct a security audit of the token and its smart contract to identify potential vulnerabilities in the smart contract. Users can also utilize advanced security instruments to scan the contract for any malicious code.
How Can Delta6Labs Help Identify & Mitigate the Risk of Honeypot Scams?
Delta6Labs has an experienced data security and audit team that conducts regular checks to identify malicious code in smart contracts and bugs in blockchains. We also conduct thorough token testing, including tokenomics, liquidity, transaction history, and sell and buy orders, before providing any insights to our clients. We also utilize various security tools to identify honeypot scams and other vulnerabilities in smart contracts.
Conclusion
Everything that has a digital footprint is not entirely safe from cyberattacks and malicious scams. The cryptocurrency industry, the most advanced sector in the finance industry, is also known for its emphasis on user privacy and the democratization of finance; however, it is also vulnerable to various types of scams, including honeypot, rug pull, and Crocodilus malware, among others.
To avoid these attacks, one can take the following steps: DYOR (Do Your Own Research), seek help from security audit firms, and stay informed about scams.
Frequently Asked Questions
Disclaimer:
The information on this blog is for knowledge purposes only. The content provided is subject to updates, completion, verification, and amendments, which may result in significant changes.
Nothing in this blog is intended to serve as legal, tax, securities, or investment advice of any investment or a solicitation for any product or service.